Module 5
Network Security
Unit 3
Vulnerability Assessments
Learning Outcomes
- Select and explain which assessment regime to use based on the type and size of the target business.
- Utilise open-source scanning and testing tools to perform vulnerability tests and scans.
- Analyse scanning results and make recommendations to mitigate vulnerabilities.
e-Portfolio Activity: Scanning Activity
Using the website(s) assigned to you in Unit 1, carry out the following exercises and answer the questions listed below. Perform a basic scan using standard tools such as traceroute, dig and nslookup. Use these basic tools and make a list that details the following information:
Response:
1. How many hops from your machine to your assigned website? Which step causes the biggest delay in the route? What is the average duration of that delay?
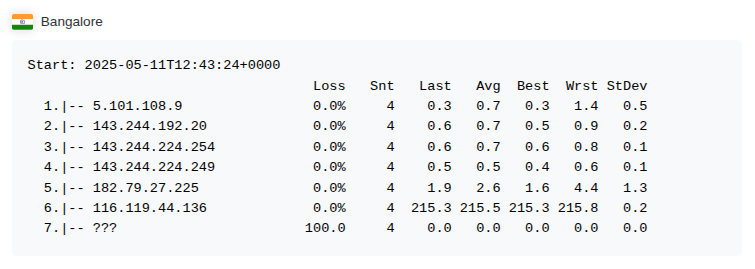
- At least 6 hops before the trace was blocked or dropped.
-
The biggest delay is at hop 6: IP
116.119.44.136. The average delay there is 215.5 ms. - Source: KeyCDN
2. What are the main nameservers for the website?
- ns1.softwaregrp.com: IP
130.57.12.53 - ns2.softwaregrp.com: IP
143.186.121.53 - ns3.softwaregrp.com: IP
192.31.114.53 - Source: WHOIS Domain Lookup
3. Who is the registered contact?
- The domain is registered through SafeNames Ltd., and the registrant organisation is listed as Open Text Corporation.
- Source: WHOIS Domain Lookup
4. What is the MX record for the website?
- The domain does not have any MX records.
- Source: WHOIS Domain Lookup
5. Where is the website hosted?
- The hosting server is located in Ashburn, Virginia, USA
- Source: Gridinsoft LLC
Vulnerability Audit and Assessment - Baseline Analysis and Plan
- An initial analysis of Zero Bank was conducted, and a 600-word analytical document was submitted. This document included key sections outlining potential vulnerabilities within the website, recommending several vulnerability assessment tools, and proposing a tentative timeline for future audits. Link to the analytical document: here
Reflection
- This unit featured two key activities: a scanning activity and an assessment, both of which are relevant to the Unit 6 assessment. I utilised online vulnerability analysis tools for both tasks to avoid impacting my personal system.